
Would you hang a van Gogh in your house and only lock your front door? This situation is similar to what many companies do every day – they lock the front door with a firewall to protect their own assets, their van Gogh. But you forget – there are many ways into the house and once inside, the van Gogh is as good as gone.
The outbreak of the Corona crisis, with the mass transfer of employees to home offices, has once again highlighted the advancing mobility and high demands of the modern workplace and underscores what many already know, but some may not want to admit: The battle to protect corporate assets has long since moved beyond the corporate network firewall to the Internet, the cloud and the home office. If you only try to protect the perimeter of your corporate network, you must feel like Don Quixote tilting at windmills. A Zero Trust Architecture (ZTA), on the other hand, addresses precisely these problems, which hardly seem to be solvable with classic approaches.
What exactly does Zero Trust mean?
The classic approach is the perimeter-based approach: firewalls, intrusion detection and network segmentation are used to protect the outer boundaries of the corporate network. If one is within this perimeter, one can then often move very freely, thanks to the design philosophy of an open corporate network. Problem is, this is just as true for attackers, hackers and ransomware. This contrasts with the zero trust approach, which should not be understood literally (“no trust”), but rather means that trust is not granted for no reason, but only in the context true to the security principle of authenticating everything and everyone. The zero trust approach is data-centric in this regard: Every data flow must prove its legitimacy through authentication and authorization, regardless of whether a user accesses an application, machines or servers communicate with each other, or services, sensors or functions.
Deep dive with Siemens: Opportunities & challenges presented by Zero Trust
“In the past, the cloud was deemed to be insecure, but today this is exactly where security development is taking place,” says Thomas Müller-Lynch from Siemens. Find out here how he took the path to the cloud at an early stage with his team and the consultants from Comma Soft and what further developments Siemens is aiming for as a cyber security pioneer.

Zero Trust as a challenge for the entire IT
The very point of the enterprise network illustrates how disruptive the topic of Zero Trust can be for an IT organization. The challenges here are huge, because: Zero Trust is not a product, service or technology that can simply be introduced or migrated to in the short term; it is an architectural picture based on certain principles, e.g., the very principle that per se no data flow is automatically trusted. The introduction or change to a ZTA can also take years, depending on the company, and is more of a program than a single project, because the integration of processes, systems and infrastructure takes time. Likewise, a number of prerequisites must also be met in order for a Zero Trust approach to even be meaningfully pursued, such as the company having a clear self-view of its physical and virtual assets, its processes and its digital artifacts, or the presence of certain IT security. The introduction of Zero Trust requires the support of the entire IT organization of a company due to the diversity of topics and always means a tightrope walk between usability vs. security and between integration of existing solutions vs. complete re-design or greenfield approach. This complexity and the effort involved often appear to be an almost insurmountable hurdle and are therefore a deterrent, although it is obvious what is at risk: the infrastructure, all IT assets and, above all, the data of the entire company.
Zero Trust: Our approach with structure
Especially for a program of this scope, important strategic considerations should be addressed early and clearly, e.g.:
What capacities in the IT organization do I need and what capacities do I have? In addition, the fundamental paradigm of the approach must also be defined, which depends individually on the character of the company: Bring about fundamental changes in solution providers or maximize use of existing solutions? Step-by-step approach or large-scale greenfield solution?
To implement a ZTA architecture, it helps to focus on the relevant pillars of a zero trust:
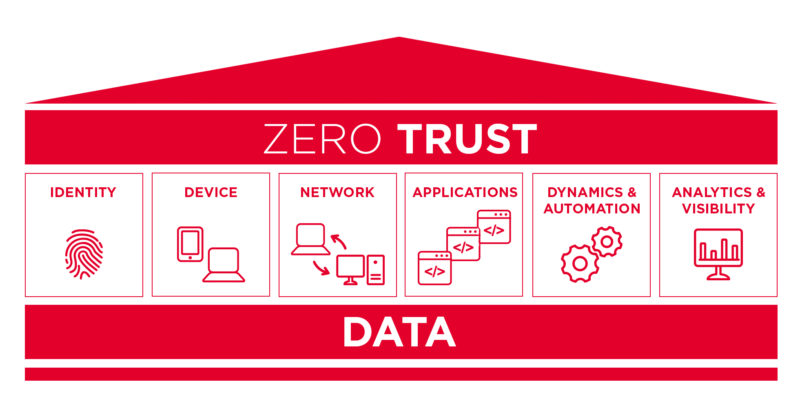
Because in the end, Zero Trust is nothing more, but also nothing less than making a dynamic decision every time data is accessed (e.g. based on trust scoring) and enforcing the decision.
At Comma Soft, we take the following steps, which promise rapid effectiveness while pragmatically attempting to reduce the complexity of the Zero Trust issue:
- Identify stakeholders of the company, because in the end they would have to be able to work flexibly with the ZTA and fulfill their business requirements.
- Identify the company’s IT assets: You can only protect and design a solution for what you know, e.g., laptops, servers, smart phones, IoT devices, but also accounts/identities, data/algorithms and applications.
- Identify key processes and risks: Understand business processes and data flows and their relationship to identify candidates for initial ZTA transition (start small with low risk).
- Establish intermediate goals: Getting to a full ZTA directly is often impossible. Therefore, it makes sense to define intermediate goals that show the way to Zero Trust and enable measurability of progress.
- Formulate ZTA Minimum Viable Product (MVP): A pragmatic approach is to define a ZTA MVP with which to learn how to run with Zero Trust in the enterprise and get an initial benefit. The definition of the MVP then incorporates which use cases are relevant to the enterprise, what information is needed for trust scoring, which architectural approaches (enhanced identity governance, micro-segmentation, software defined perimeter) and architectural variations (agent & gateway, enclave, resource portal, sandboxing) make sense.
- Identify solutions: Get an overview of which solution can solve which problem and decide (e.g., which solution can serve as policy decision and enforcement point).
- Go live with MVP and gain experience: Learn and continuously improve the MVP.
- Extend ZTA MVP to full solution: Integrate additional assets and processes and scope and e.g., trust scoring
extend
Our approach with added value
Our approach using an MVP combines the advantages of rapid effectiveness and operationalization, i.e. having a real solution at hand and approaching the topic of zero trust pragmatically with a focus on benefits. Strategic interim goals help to keep an eye on profitability, which plays a particularly important role in security projects. Even if the goal of Zero Trust has not yet been achieved, improvements already achieved in the areas of security, identity & access management, monitoring and authentication can be seen from them at any time. We believe that this transformation to a ZTA requires a high degree of individuality in order to specifically address each individual company and its hurdles in the area of Zero Trust. Added value is created where a ZTA interacts with the business and its processes to enable value creation together with security, not where the business has to adapt to the solution. Comma Soft brings extensive expertise to the table, ranging from IT strategy, project and program management, change management, architecture and security to technical issues around identity & access management, access control, cloud solutions and monitoring. This expertise is the result of our long-standing role as trusted advisor in IT, security and transition projects for many SMEs as well as large DAX companies.

