Travel report #02
Our Humboldt editorial team is on the road again and this time they are reporting back to you:
- How the exciting journey to ALAN, our own Generative AI, went.
- Why the motto should be Zero Trust in the face of new cyber security risks.
- The importance of the Petersberger Gespräche as a salon for business, technology and science.
- What moves our crew members in their work at Comma Soft and beyond.
Enjoy reading and discovering!
If you are interested in more information about our GenAI and cyber security solutions beyond this travelogue, you will find more exciting information on this page. Have fun discovering!
We would also like to invite you to get in touch with us: For questions, suggestions, to exchange ideas – write to us and we will get back to you!

Large Language Models
Large Language Model – LLM – Generative AI – Prompting: The terminology can be confusing. If you want to delve deeper into the topic, you can find more details on the most important terms here.
-
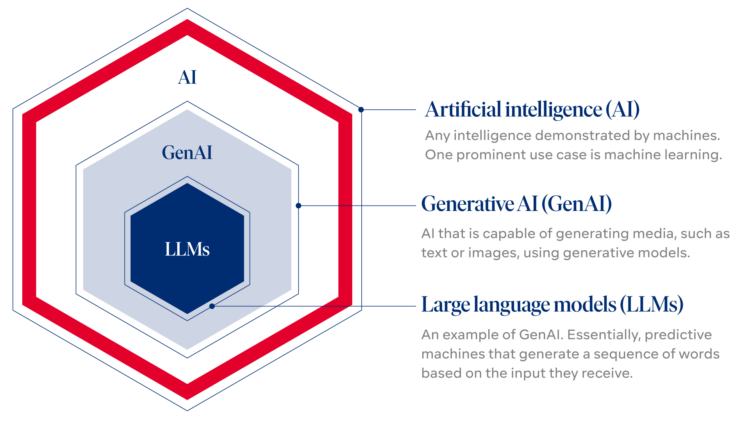
Any form of machine intelligence is referred to as artificial intelligence (AI). In common parlance, the term artificial intelligence is used when a machine imitates “cognitive” performances such as learning and problem solving, which are otherwise associated with human mental performance. AI is an area of computer science research in which intelligent machines are developed and studied. An important area of modern research into artificial intelligence is machine learning: Here, the machine learns to classify images or predict time series with the help of huge amounts of data.

Meet ALAN!
Would you like to get to know ALAN? Dr. Andrej Fischer and Michael Tannenbaum will be happy to show you our LLM in a personal live demo. You can find more information and book your demo appointment here.
Further reading tips for you
We are all always interested in keeping up to date with technological and ML/LLM trends. If you also want to dive deeper, we recommend the following literature:
- “Attention Is All You Need”
This paper is the starting point for the modern development of LLMs. It introduces the Transformer architecture and is a must-read for anyone interested in the technical foundations of LLMs.
- “We have no moat and neither does OpenAI”
Leak from a Google researcher, on the expected superiority of open source language models.
- “Eagle 7B : Soaring past Transformers with 1 Trillion Tokens Across 100+ Languages (RWKV-v5)”
Publication of the Eagle 7B model, a promising language model that works without an attention mechanism.
- Open source models in comparison
If you are looking for an overview of the currently available open source models, you will find what you are looking for here.
- Petersberg Theses on AI
An exciting format that discussed the social impact of artificial intelligence long before the advent of generative AI.

Zero Trust
Zero Trust is the security approach required today, which we implement with our customers in SMEs and corporations. In the white paper, Dr. Jan Ciupka provides even deeper insights into the concept and its architecture. We have also gone through a classic attack case, known as data poisoning, for you here. You will also find a checklist that you can use to check what the next steps are for your company in terms of cyber security.
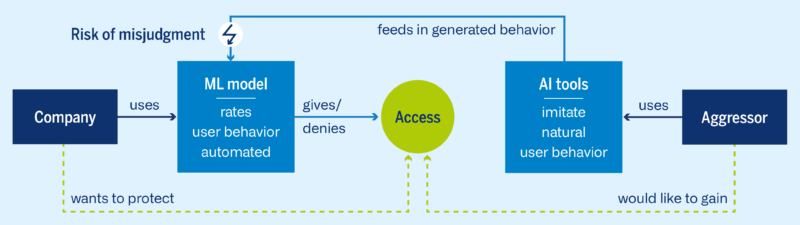
Data poisoning
As you can see from the illustration, the attack in data poisoning starts with the data used by the ML model. If an ML model is trained with open source data, for example, attackers could manipulate this data. This means that the AI can be maliciously trained if it no longer uses truthful data, but data that deliberately leads the AI down the wrong path. Data poisoning is a high cost factor for affected companies that have invested in training their ML models. It can also be a gateway for hackers to gain access through targeted manipulation. The potential consequences for companies are well known. Data poisoning can be prevented above all with the right cyber security strategy.
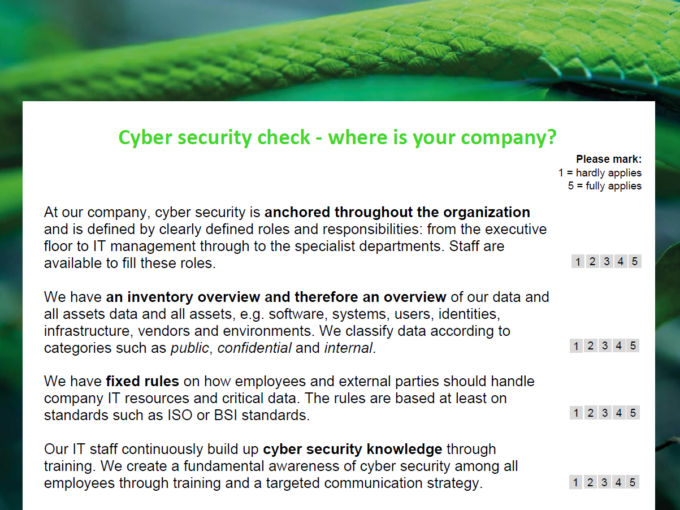
Take the cyber security check!
Do you want to check how secure your company is? This checklist will help you to identify risks and derive measures.
What exactly does Zero Trust mean?
In this white paper, our colleague Dr. Jan Ciupka has compiled for you what the cornerstones of Zero Trust are and what companies should bear in mind when implementing them.
Deep-Dive with Siemens: Opportunities & Challenges of Zero Trust
Siemens is one of the first companies to adopt a zero trust approach to IT and cyber security. What opportunities does this present for the Group’s security and for the further development of its products?

Petersberger Gespräche 2023 – The Salon for Business, Science & Technology
Watch the review video of the Petersberger Gespräche 2023 (available in German):

If you would like to know which topics and speakers have shaped the program in the past, take a look at the Dialogue Forum’s YouTube channel.

AI Playlist
Would you like to try out (Gen)AI for yourself? If you are interested, please contact us to arrange a demo for Alan. We have also put together a hit list of exciting AI applications for you to try out. Have fun!

The journey continues!
We have already set sail again and are continuing to explore new worlds.
Would you like another copy of the current report or would you like to register yourself and your colleagues for the next issue? Write to us!