
Secure identity management with Microsoft Solutions: Protecting identities across on-premises and cloud environments
We’ve all heard it countless times: “The world is becoming more and more interconnected.” Users rely on their digital identities to access a wide range of applications and services. As the number of these applications continues to grow, safeguarding these identities has become increasingly critical for companies aiming to minimize the risk of cyberattacks. In this article, we introduce Microsoft solutions that provide comprehensive protection – on-premises, in the cloud, and in hybrid environments.
Many companies are already familiar with digital identities in the on-premises environment, mainly through Microsoft’s Active Directory (AD) directory service. However, in the cloud world, identities are just as essential. While some of these identities are the same as those in AD, there are also others. Both must be protected, as they can both be targets of cyberattacks. When identities from the cloud and on-premises environments overlap, they may become even more appealing targets for attackers. Companies might feel confident that they’ve taken all necessary steps to secure their identities in on-premises Active Directory (AD). However, they may have overlooked the cloud attack vector. The opposite can also be true. This is precisely where Microsoft Defender XDR comes into play.
What is Microsoft Defender XDR?
Microsoft Defender XDR is a comprehensive security solution that integrates various Microsoft security products and services into a unified platform, including tools like Microsoft Defender for Identity and Entra ID Protection. Whether a company aims to secure identities in the cloud, on-premises, or in a hybrid environment, Defender XDR provides tailored solutions or a combination of them for effective threat detection, defense, and response. A range of protection mechanisms, including endpoint protection, network security, and threat analysis, are employed to deliver a comprehensive view of a company’s security posture. By leveraging artificial intelligence and machine learning, Microsoft Defender XDR enhances the speed and accuracy of threat detection and mitigation. This positions it as a robust solution for defending against modern, sophisticated cyber threats.
Specialized tools for professionals
Assembling a simple shelf from a popular Scandinavian furniture store often only requires the small hexagonal wrench that comes with it – a versatile tool for basic tasks. However, when it comes to constructing an entire house, more advanced tools are essential. The same principle applies to corporate cybersecurity: when numerous identities are at stake, managing security can quickly become overwhelming. That’s where professional tools like Microsoft Defender for Identity and Entra ID Protection can really help.
Why does Microsoft provide two products for safeguarding digital identities?
Both Microsoft Defender for Identity and Entra ID Protection are available, but they serve fundamentally different purposes. To stick with the analogy: it’s not just a hex wrench; it’s both a hex wrench and a Phillips screwdriver.
Microsoft Defender for Identity
Microsoft Defender for Identity is specifically tailored to detect and prevent threats within on-premises environments, particularly in traditional Active Directory setups.
The solution employs sensors that are installed directly on the domain controllers (DCs) to gather activity data. However, this data is analyzed in Azure rather than on the domain controller itself. This approach ensures that the performance of the DC is not significantly impacted, allowing alerts to remain accessible even if the controller is compromised. The collected data, including Windows events, information from RADIUS (VPN), and details about users and computers, is utilized to establish a behavioral baseline and categorize threats along a “kill chain.”
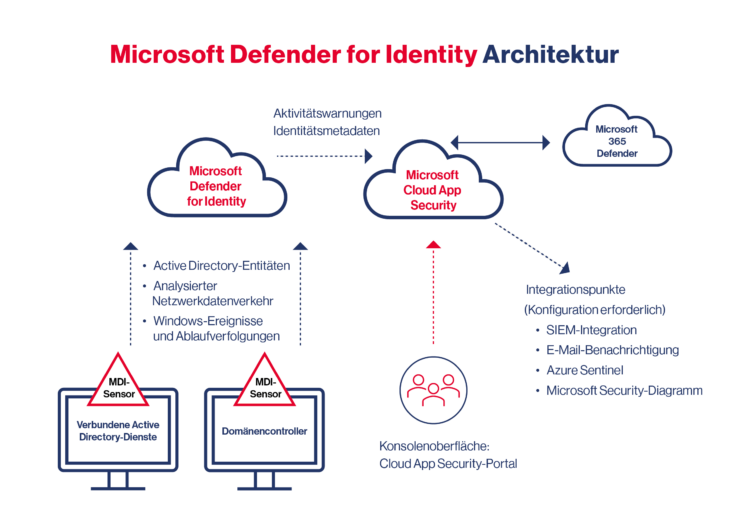
The concept of the kill chain in relation to Active Directory is a well-established model, akin to the cyber kill chain. In the context of Active Directory (AD), it outlines the typical steps or phases an attacker follows to compromise an AD environment. These phases are as follows:
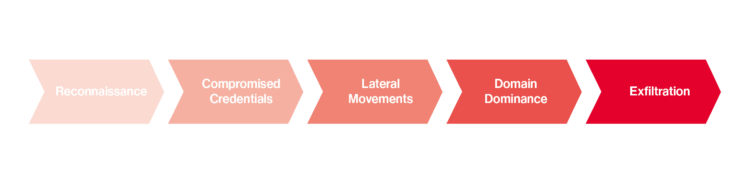
- Reconnaissance: Gathering information about the Active Directory structure, including user accounts, groups, and other relevant data, to identify potential vulnerabilities.
- Compromised Credentials: Acquiring valid access credentials, such as through attacks on the Kerberos ticket system or phishing schemes.
- Lateral Movement: The attacker navigates through the network, gradually gaining more privileges, often employing techniques like “pass the hash” attacks.
- Domain Dominance: The attacker achieves control over the domain by taking over one or more domain controllers. This is where the Azure evaluation provides a significant advantage: you retain access to the data collected by the Defender for Identity Sensor, as the analysis is conducted in the cloud.
- Exfiltration: An attacker will naturally want to secure the data they have gathered. To do this, they need to transfer it outside the AD network. Microsoft Defender for Identity can detect large volumes of data transfers, suspicious logs, and unusual targets, helping to prevent data exfiltration.
Entra ID Protection
The Entra ID Protection solution is designed to safeguard cloud-based identities within Entra ID (formerly Azure AD). It assesses risk levels – such as user risk and sign-in risk – to evaluate the likelihood of an identity being compromised. Based on these evaluations, it can automatically implement countermeasures, such as blocking an account or requiring multi-factor authentication (MFA) when suspicious login attempts are detected.
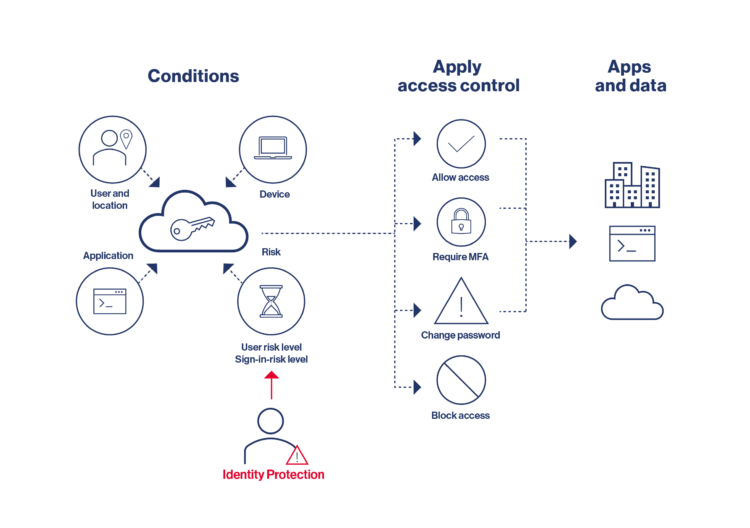
- Risk Levels: These indicate the potential risk of a user account being compromised. Alerts may be triggered by factors such as unusual login locations or exposed credentials.
- Remediation: Based on the risk assessment, predefined actions are triggered, which can be executed either by the users themselves or by administrators.
- Risk-based Conditional Access Policies: These policies are informed by the identified risks and allow for actions such as requiring multi-factor authentication (MFA) for suspicious login attempts instead of outright blocking the account.
Security for every scenario
Both Microsoft Defender for Identity and Entra ID Protection are crucial components of a robust security strategy within the Microsoft ecosystem.
Microsoft Defender for Identity is especially well-suited for organizations that maintain an on-premises infrastructure using Active Directory and seek to quickly detect and neutralize threats within their corporate network.
Entra ID Protection, on the other hand, is essential for organizations that utilize cloud services and want to safeguard their identities in Entra ID from modern threats. It provides proactive monitoring and automated responses to suspicious activities, which is especially crucial in a cloud-based environment.
Companies with a hybrid infrastructure should leverage a combination of both solutions, as together they create a robust defense.
If you’d like to explore this topic further or need assistance with implementation, please reach out to Tobias Wurm and his team.











